
Azure AD Application proxy is a really nice way to give remote access to on-prem hosted web site that haven’t yet been moved into the cloud and can be uses with Intune on mobile iOS and Android devices and can even redirect internal URLs to App proxy URLs for a seamless user experience.
Though if you are still using ADFS on-prem for authentication to claims based apps it can become a real pain to get working as the Microsoft advise is to have the authentication to ADFS happen outside of AAD App Proxy that may not be possible for secure networks. the diagram below shows how that authentication would work.
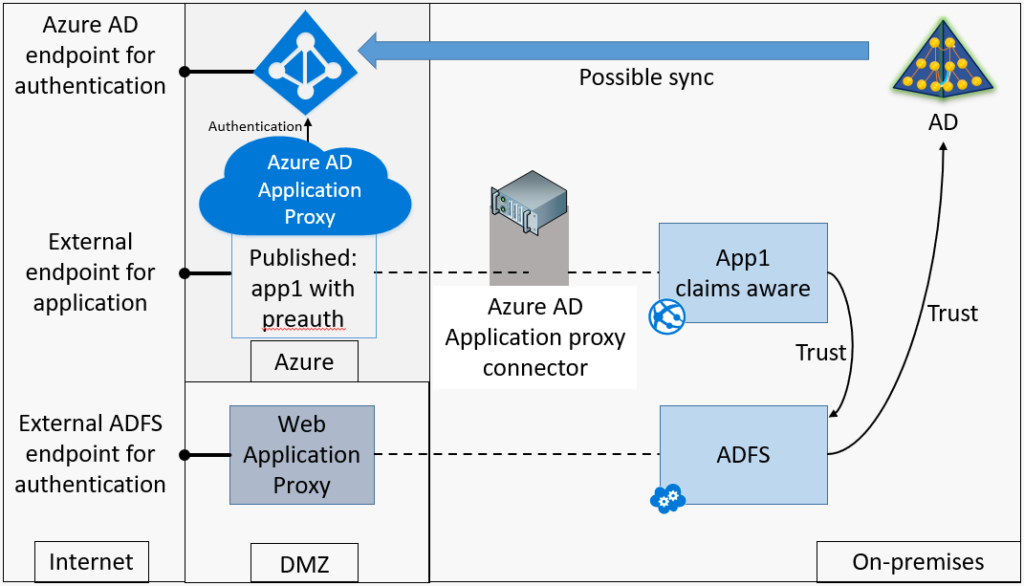
The issue you may find is that for this to work ADFS must allow external logins to you claim applications that in a secure network may not be allowed.
Your next step maybe to try and publish your ADFS sts websites so the authentication happens from within your network. the diagram below shows how that authentication would look.
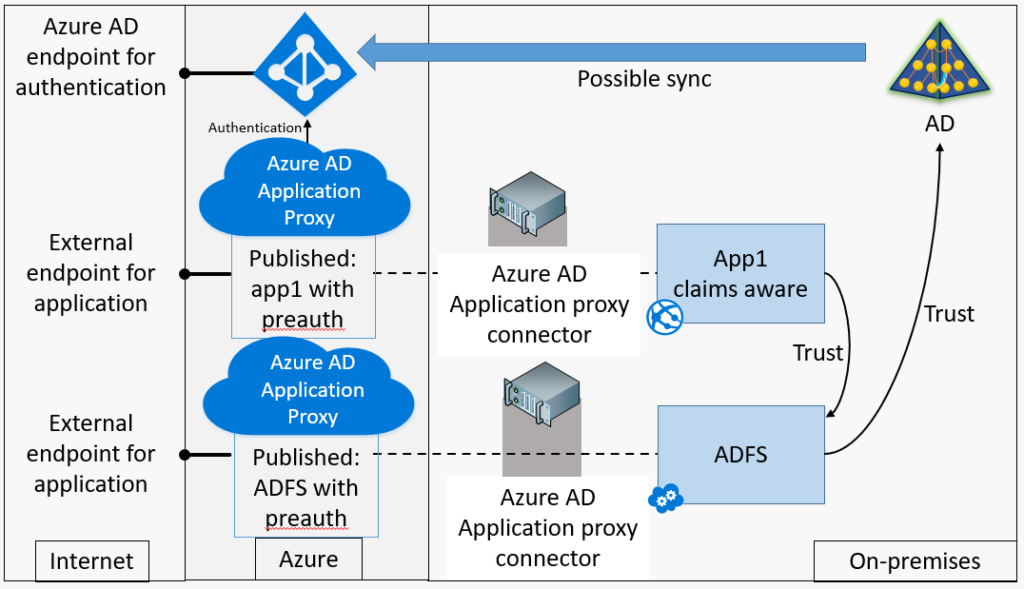
though if you have your Access Control Policy set to “Permit everyone for intranet access” this will fail even though the authentication is happening from within the network and the AAD App Proxy servers are resolving to the internal ADFS Servers.
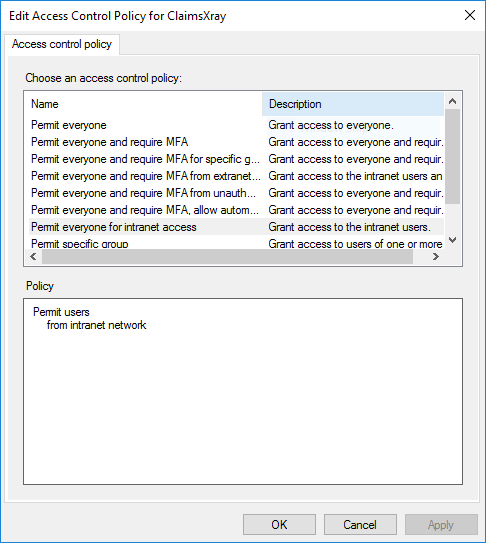
Within the logs on the ADFS Server you will see that the claims request will come into ADFS and start to process the policy
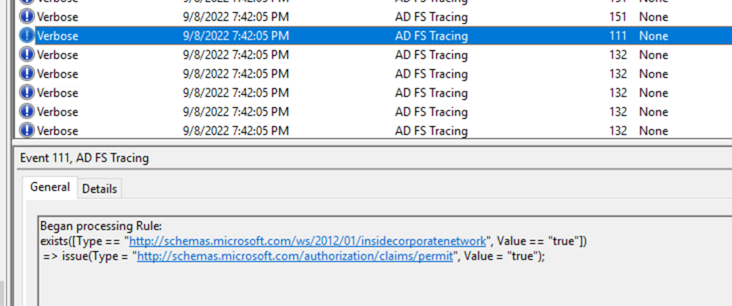
The output claim will be empty that means that it didn’t meet the requirement (insidecorperatenetwork) that is part of the “Permit everyone for intranet access” rule
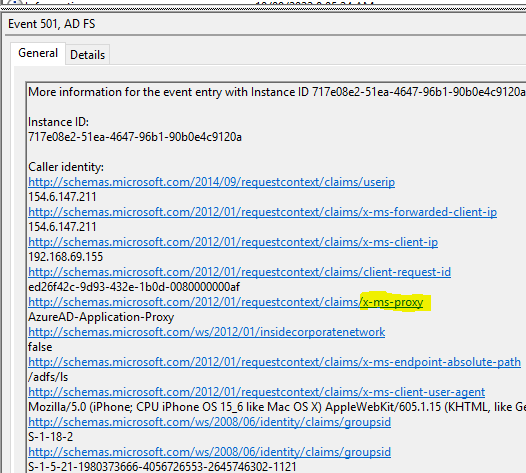
this is due to the request also coming in with the x-ms-proxy been marked, my theory on why this is getting marked on the request is that Microsoft have pulled from the same code used for ADFS WAP as they have for AAD App Proxy.
Now onto a solution for allowing requests from the AAD App Proxy Servers without setting the Access Control Policy to “Permit everyone” that would also only allow authentication externally through the AAD App Proxy Server and block the ADFS WAP Servers.
Using a Issuance Authorization Rule with the ADFS claim rule system to build a rule that will.
- block requests marked with the x-ms-proxy claim
- exclude the IP addresses of the AAD App Proxy servers based on the x-ms-client-ip claim
- allow all users that do not apply to the first rule or are excluded
Before we can use a Issuance Authorization Rule we much change the Access Control Policy into a Issuance Authorization Rule and add a blank claim to allow editing. this can be done with a couple lines of PowerShell.
The first command gets the Relaying Party Trust that you would like to edit, the next set the Access Control Policy to Null
$ADFSTRUST = Get-AdfsRelyingPartyTrust -Name "Name of App"
Set-AdfsRelyingPartyTrust -TargetRelyingParty $ADFSTRUST -AccessControlPolicyName $null
Now when you go to edit the Access Control Policy you will see a blank rule
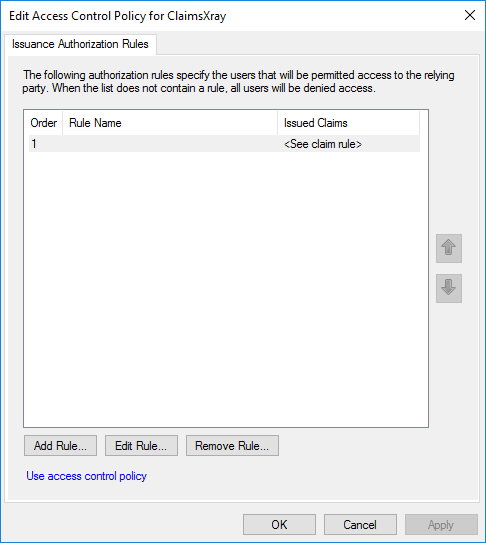
Now to make our rule, We want to block requests that are coming from application proxy like ADFS WAP and exclude the AAD App Proxy servers
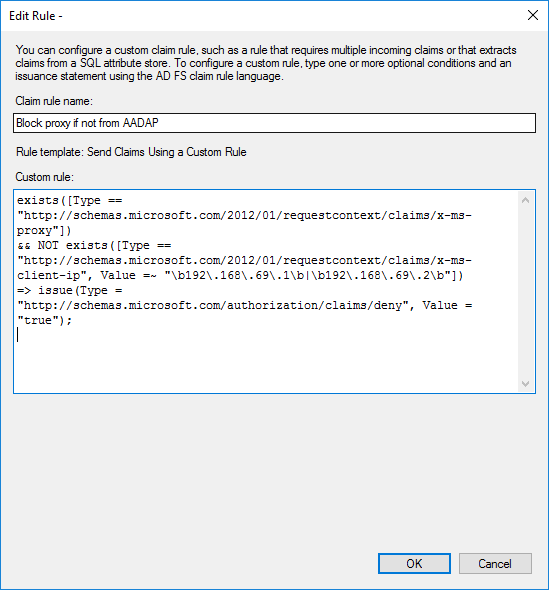
I have done this with the rule below
exists([Type == "http://schemas.microsoft.com/2012/01/requestcontext/claims/x-ms-proxy"])
&& NOT exists([Type == "http://schemas.microsoft.com/2012/01/requestcontext/claims/x-ms-client-ip", Value =~ "\b192\.168\.69\.1\b|\b192\.168\.69\.2\b"])
=> issue(Type = "http://schemas.microsoft.com/authorization/claims/deny", Value = "true");
this line is looking for if a app proxy is in use “exists([Type == “http://schemas.microsoft.com/2012/01/requestcontext/claims/x-ms-proxy”])”
this next line is then excluding the IP addresses of the AAD App Proxy servers, in this example the IP address of the servers are 192.168.69.1 & 192.168.69.2, the | is an or statement within the rule. allowing a number of servers to be added if required. regex can also be used if a high number of IP addresses need to be added to the rule. “&& NOT exists([Type == “http://schemas.microsoft.com/2012/01/requestcontext/claims/x-ms-client-ip”, Value =~ “\b192.168.69.1\b|\b192.168.69.2\b”])”
the last part of the rule is to deny requests that are not excluding in line 2, E.g ADFS WAP Servers. “=> issue(Type = “http://schemas.microsoft.com/authorization/claims/deny”, Value = “true”);”
Then add a Permit All users rule to allow any request that isn’t coming from the ADFS WAP servers. E.g intranet users.
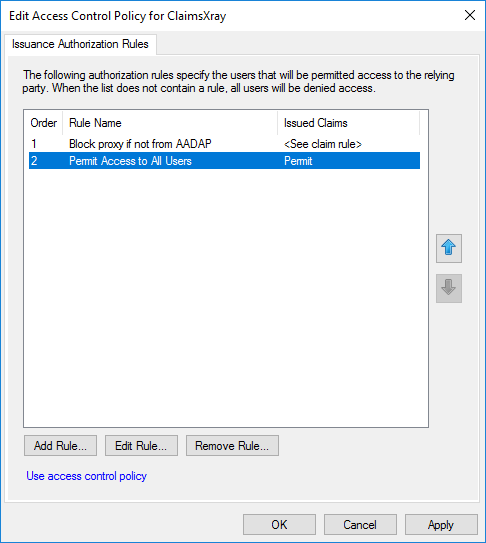
You should now be able to have users using AAD App Proxy be able to login to Web Applications from their devices but still be blocking external access to ADFS / the applications.
Do note that SSO within the setup will not work and users will need to logon with a username and password, they will have the authorization token saved onto their device for a windows of time that will allow them to logon to other applications without the need to login again.